| 3DES |
Triple Data Encryption Standard: A method of encryption (168 bit). |
| AAA |
Authentication, Authorisation, and Accounting: Security system Authentication proves who you are, Authorisation says what you can do, and Accounting logs what you have done. |
| AAC |
Advanced Audio Codec: A file format for storing music in ‘lossless’ quality. Used heavily by Apple. |
| ACE |
1. Access Control entry: One element of an ACL
2. RSA ACE Server is the old name for RSA Authentication Manager. |
| ACL |
Access Control List:Rules applied on a network device that allow communication over numbered ports to and from certain IP addresses. |
| AD |
Active Directory: Introduces with Windows Server 2000, this is Microsoft’s domain directory services role. |
| ADAM |
Active Directory Application Mode: This was replaced in Server 2008 with LDS |
| ADK |
Windows Assessment and Deployment Kit: A suite of tools for customising and deploying Windows operating systems, has replaced the WAIK. |
| ADMX |
A file extension used for files that can be imported into Microsoft Group Policy Objects. |
| ADSL |
Asymmetric Digital Subscriber Line: An internet connection ran over copper wire (usually a telephone line). It tends to have faster download than upload speed. |
| AES |
Advanced Encryption Standard 128,192, or 256bit. |
| AH |
Authentication Header: A member of the IPSec suite of protocols provides integrity and authentication of data packets. |
| AMD |
Advanced Micro Devices: A company that makes microprocessors and CPU’s. Main rival to Intel. |
| AP |
See WAP |
| API |
Application Programming Interface: Allows software to talk to other software. |
| ARP |
Address Resolution Protocol: A network protocol used to translate physical addresses to IP addresses, and vice versa using RARP (Reverse ARP). |
| ASA |
Adaptive Security appliance: Range of Cisco firewalls. |
| ASDM |
Adaptive Security Device Manager: Web management console for Cisco firewalls running OS 7 and above. |
| ATA |
Advanced Technology Attachment: Used to connect drives to a computer. |
| ATM |
Asynchronous Transfer Mode: Used to move computer data, video, or audio over a network. It embeds the data in ‘cells’ which all travel along a fixed path to their destination. This differs from TCP/IP ‘packets’ which can travel over many different routed to their destination. |
| AV |
Anti Virus. |
| AVI |
Audio Video Interleave: A File format used for video files. |
| BBWC |
Battery Backed Write Cache: A small power source that lived on a hardware RAID controller, the battery supplies power to the cache so in the event of power loss, information that is about to written to disk is not lost. |
| BIND |
Berkeley Internet Name Daemon: DNS software commonly used in Unix and Linux distributions. |
| BIOS |
Basic Input Output system: This is bootable firmware that live on most modern PC’s and Servers you access this before the OS loads usually by pressing F1, F2, F10, or Esc. |
| BITS |
Background Intelligent Transfer Service: A system that uses idle bandwidth to download data (usually updates). |
| BSOD |
Blue Screen Of Death: Seen on a Windows Machine after a crash, if it has not been set to reboot in the event of a crash, it takes it name from the blue background and white text. (Also see PSOD). |
| BSSID |
Basic Service Set Identifier: A unique name that specifies a wireless access point or router. Used in an Infrastructure wireless network *See SSID and ESSID) |
| BT |
British Telecom, the largest ISP in the UK, |
| BT Syndrome |
You have an Internet problem, so you ring BT, they tell you they cant see anything wrong, and magically it starts working while you are on the phone. |
| CA |
Certification Authority: An entity that produces digital certificates. |
| CAL |
Client Access Licence: A Licence used to access server services, used a lot on Microsoft Networks where licenses are “per seat”, “per user”, or “per device”. |
| CAS |
Client Access Server: A role used by Microsoft Exchange server. A CAS server typically runs OWA and ActiveSync |
| CCNA |
Certified Cisco Network Associate: Entry level Cisco networking qualification. |
| CCMP |
Counter Mode/CBC-MAC Protocol: Security system that uses a 128 bit key for encryption. Seen on HP Wireless controllers. |
| CCO |
Cisco Connection Online: You can create a login free at Cisco to log into this service, once set up you can add valid support agreements to you account to enable you to get support and download updates. |
| CCP |
Cisco Configuration Professional: A Java based graphical management software tool for deploying and configuring Cisco Routers, and wireless access points etc. |
| CCR |
Cluster Continuous Replication: Introduced in Exchange 2007, this provides a second copy of the exchange database that can be used in a disaster recovery situation. |
| CD |
Compact Disk |
| CGI |
Common Gateway Interface: A method use to both generate dynamic web content, and pass information between a web server and a browser or application a visitor is using. |
| CHAP |
Challenge Handshake Authentication Protocol: Used to authenticate a remote user or hot. |
| CIFS |
Common Internet File system: A Microsoft system for sharing files on a network that was developed from SMB. |
| CLI |
Command Line Interface: The command interface for various network devices, usually accessed by a console cable SSH or Telnet. |
| CMOS |
Complementary Metal Oxide Semiconductor: this is actually a technology used in integrated circuits, but some people still refer to a machines BIOS/RBSU as CMOS |
| CN |
1. Common Name: {digital certificates} When a digital certificate is signed by a CA, this proves the common name (the name presented on the certificate) is correct.
2. Common Name: {Active Directory AD} The name of an object in active directory i.e. “CN=Fred Bloggs”. |
| CODEC |
COder-DECoder (or Compressor-DECompressor). A small piece of software that lets a computer “Understand” a particular video/audio encoding. |
| cPanel |
cPanel is a suite of tools that a company hosting your website can provide you access to, to manage your own website. It is used on Apache web servers |
| CPU |
Central Processing Unit: The “Brain” and main chip that provides a machines number crunching capability. |
| CRL |
Certificate Revocation List: Is a list published by a CA for certificates that have been cancelled or revoked. It uses OCSP. |
| CRM |
Customer Relationship Management: A system used primarily by sales marketing, and customer services. It’s usually a database of customers and potential customers. |
| CSC |
Content and Security Control: A Plug in module for ASA 5510 and above platforms that provides scanning and anti spam facilities from an embedded Trend Micro Server. |
| CSE |
Client Side Extensions: A set of extra GPP settings built into Windows 7, (need to be manually installed on older versions of Windows) |
| CSR |
Certificate Signing Request: A request sent to a CA to apply foe a digital certificate |
| CSV |
Comma Separated Values: A common file format that can be opened by Microsoft Excel. Also used for importing and exporting bulk data. |
| CSVDE |
Comma Separated Value Data Export: A method of bulk importing or exporting data from a CSV file to perform a task – commonly used for bulk import/export of users or computers with AD |
| DAG |
Database Availability Group: A system used by Microsoft Exchange to maintain database availability by keeping copies of the mail database(s) on different mail servers. |
| DC |
Domain Controller: The logon server that’s present in Microsoft Server domains. |
| DES |
Data Encryption Standard: A method of encryption (56 bit) is considered very weak for modern communication – in 1999 it was broken in 22 hours and 15 minutes by the EFF |
| DH |
Diffie Hellman: A system used to swap keys securely over a public network. |
| DHCP |
Dynamic Host Configuration Protocol: A method used to lease an IP address to a device so it can communicate on a network. |
| DMZ |
De-Militarised Zone: A network segment attached usually to a less secure network, traditionally the home of web servers and edge servers. |
| DNS |
Domain Name system: The system that translates network names into IP addresses. |
| DNSBL |
DNS based Block List (or Black-hole List depending on what documentation you read) Is dynamic list of known email spammers. |
| DS |
Directory Services: Using a central repository of network assets for management |
| DSL |
Digital Subscriber Line: A network connection, usually to the internet, the speed of traffic “down” is usually fast, and the speed of traffic “up” is slow, this makes it ideal for home internet connections. |
| DSN |
Data Source Name: Usually used with ODBC connections these refer to a data source (usually a database). |
| DVD |
Digital Versatile Disk or Digital Video Disk |
| DVDROM |
Digital Versatile Disk or Digital Video Disk Read Only Memory |
| EAP |
Extensible Authentication Protocol: Used with both wireless protocols like WPA, it’s part of the PPP suite of protocols |
| ECC |
Error-Correcting Code Memory: Typically more expensive than normal RAM, it uses a parity system to error check corruption in the data it holds. |
| ECP |
Exchange Control Panel: Web based administrative console for Exchange, it was brought in with Exchange 2010. With Exchange 2013 the Exchange Administrative Center runs form the same location. |
| EDNS |
Extension mechanisms for DNS: Essentially DNS but in network packets greater than 512KB |
| EFF |
Electronic Frontier Foundation: Non profit US organisation. |
| EMC |
Exchange Management Console: The Graphical user management console for Microsoft Exchange. |
| ePO |
e Policy Orchestrator: McAfee’s product for managing deployment and updates to its anti virus products. |
| EPT |
Extended Page Tables: A technology used by Intel VT-x for CPU virtualization. |
| ESMTP |
Extended Simple Mail Transfer Protocol (SMTP) As users wanted to send extra data attached to their emails, this system was developed to let that happen. It lets a client and mail server negotiate what capabilities it can use. |
| ESP |
Encapsulation Security Payload: A member of the IPsec suite of protocols provides authenticity integrity and confidentiality of data packets. |
| ESSID |
Extended Service Set Identifier is an SSID used in ad-hoc networks |
| ESX |
Originally Stood for Elastic Sky, ESX is Vmware’s hypervisor virtualisation server platform developed from GSX
the i in ESXi is is for “Integrated” and can be ran from a flash drive or chip on a PC/Server. |
| EULA |
End User Licence Agreement: the legal contract between the user and the person/company who has produced some software. Typically the EULA is the section in an install where you tick “I Agree..”. |
| FEP |
Forefront Endpoint Protection: Microsoft’s Client AV solution released 2010 |
| FQDN |
Fully Qualified Domain Name, usually a PC or servername followed by the domain DNS name i.e. server1.petenetlive.com |
| FSMO |
Flexible Single Master Operation: pronounced “Fiz-mo” These are 5 roles held by Active Directory domain controllers. |
| FSRM |
File System Resource Manager: Introduced with Server 2008 R2, this server role handles file quotas and screening rules. |
| FTP |
File Transfer Protocol: As the name suggests, a protocol for transferring files over a network uses TCP Port 21. |
| FTTC |
Fibre to the Cabinet: An internet connection that provides a fibre optic cable from either a telephone exchange (Or Comms distribution point), to the cabinets that are in the street. From the cabinet to the home/business will usually be standard copper (POTS) cable. |
| FTTH |
Fibre to the Home: An internet connection that provides a fibre optic cable from either a telephone exchange (Or Comms distribution point), directly to a consumers home or place of business. |
| GAL |
Global Address List: Used on a Microsoft Exchange server a list of email addresses generated by the server that clients can search. |
| GB |
Gig a Byte: Giga means 10 to the power 9, or 1,000,000,000 bytes, however in computing terms we work in binary so it worked out as 2 to the power 30, which equals 1,073,741,824 bytes. |
| Gbps |
Giga bits per second 9 a bit is one binary digit (0 or 1) there are 8 bits in one Byte. |
| GSX |
From its development name GSX is Vmware’s Ground Storm Virtualisation platform, was replaced by ESX |
| GPO |
Group Policy Object: This is a template used to lock down or enforce a policy on a computer or a user. |
| GPP |
Group Policy Preference: Brought in with Windows Server 2008 designed to compliment GPO network management. |
| GRE |
Generic Routing Encapsulation: A Cisco protocol for encapsulating other protocols over a network. |
| GRT |
Granular Recovery Technology: A term used by Symantec to describe their backup technology, that lets you restore a single item from a large backup job, e.g. one email from and Exchange backup, or one user from Active Directory. |
| GUI |
Graphical User Interface. |
| GUID |
Global Unique Identifier: Used to identify active directory objects, and also a hard coded serial number built into computers so they can be identified on a network when they pXe boot. |
| HA |
High Availability: An attribute given to a VMware cluster so that if any ESX host fails, it’s guest machines automatically get migrated to another host. Also the term used to describe multiple exchange databases deployed for failover. |
| HDD |
Hard Disk Drive. |
| HTML |
Hyper Text Markup Language: Is a language used to create documents on the world wide web. |
| HTPC |
Home Theatre Personal Computer. |
| HTTP |
Hyper Text Transfer Protocol: Traditionally the protocol of web pages, runs over TCP port 80, however multiple vendors abuse this by trying to get their software to run on the same port as this port is usually open on corporate firewalls. |
| HTTPS |
Hyper Text Transfer Protocol Secure: This is web traffic that is secured, using SSL |
| IAS |
Internet Authentication Server: Microsoft Implementation of RADIUS |
| ICMP |
Internet Control Message Protocol: Part of the IP suite of protocols, ICMP is used to send errors and connection states. |
| IE |
Internet Explorer: Microsoft’s web browser. |
| IESC |
Internet Enhanced Security Configuration: A Tighter set of browser stings applicable to a Windows Server. |
| IETF |
Internet Engineering Task Force: Develops and promotes Internet Standards |
| IIS |
Internet Information Server: The Microsoft web server platform, included with Windows server systems. |
| IKE |
Internet Key Exchange: A protocol used to set up SA’s in the IPsec protocol |
| iLO |
Integrated Lights Out: Let you connect to the console of a HP Proliant Server, even if its powered off, the iLO is presented as a standard RJ45 network socket on the back of the server. |
| IMAP |
Instant Message Access Protocol: Method of retrieving messages from a mail server, runt over TCP port 143 |
| IOS |
Internetwork Operating System: OS used by Cisco devices and Apple Devices. |
| IP |
Internet Protocol: A protocol for communicating across a switched network (like the Internet). |
| IPSEC |
Internet Protocol Security: A suite of protocols for securing IP communications. |
| IPv6 |
IP Version 6: Replacing IPv4 (current version which can have 2 to the power 32 (4,294,967,296) possible addresses, IPv6 uses 128-bit addresses, for an address space of 2 to the power 128 (approximately 340 undecillion or 3.4×10 to the power 38). |
| ISA |
Microsoft Internet Security and Acceleration Server: replaced MS Proxy 2.0, it provides web proxy services and Enterprise Firewall capabilities. |
| ISAKMP |
Internet Security Association and Key Management Protocol: A system for establishing Security Association and secure keys, usually used for VPN communication. |
| iSCSI |
Internet Small Computer System Interface: System used to carry SCSI commands over an IP network, used for small SAN infrastructures. |
| ISO |
A type of file format that’s used for storing CD/DVD Images, it takes its name from the International Organization for Standardization. |
| ISP |
Internet Service Provider: The Person or company that provides a link to an external network (usually the Internet). |
| ISR |
Integrated Services Router: A series of Cisco Routers. |
| IV |
Initialization Vector: Used in cryptography, its a ‘fixed size’ input. |
| IWSS |
Inter Scan Web Security Suite: A suite of products by Trend Micro, for AV and URL filtering. |
| JNLP |
Java Network Launching Protocol: Used to deliver “Java Web Start” and run an application from a web server. |
| KB |
Kilo means 10 to the power 3, or 1,000 bytes, however in computing terms we work in binary so it worked out as 2 to the power 10, which equals 1,024 bytes. |
| KMS |
Key Management Server/Service: With the release of Windows Vista/2008 Microsoft changed their software licence method. Previous VLK keys were replaced by both MAK and KMS Keys. Software with a KMS key must get its activation from a KMS server (installed on its local network) every 180 days. |
| L2TP |
Layer Two Tunnelling Protocol: Developed from PPTP used to authenticate remote VPN clients |
| LACP |
Link Aggregation Control Protocol: A protocol that allows you to bundle together more than one network link and treat it as it id is one link. |
| LAN |
Local Area Network: A computer network that connects multiple PC’s to each other and local resources. Also the inside port on a router or firewall. |
| LBFO |
Load Balancing and Fail Over: New with Server 2012, this provides NIC teaming/aggregation and standby NIC support. |
| LDAP |
Lightweight Directory Access Protocol: Designed for accessing and editing directories over an IP network, Microsoft LDAP commonly runs over TCP port 389 |
| LDS |
Lightweight directory Services: A small subset of AD that’s used for applications, (on versions of Windows before 2008 it was called ADAM) |
| LTO |
Linear Tape Open: A standard of magnetic tape storage, developed by Quantum/Seagate. Commonly used by HP, IBM and Certance |
| LUN |
Logical Unit Number: used in SAN storage, each piece of “storage” is represented by a LUN that’s presented to other devices on the storage network/fabric. |
| MAC |
Media Access Control: The “Burned in” hardware address used on all Ethernet network devices. |
| MAK |
Multiple Activation Key: A Microsoft software unlock code, designed to be used multiple times. Took over from a VLK key, its either entered manually, from a script or unattended file, or using the VAMT tool. |
| MAPI |
Messaging Application Programming Interface: A Set of standards and instructions that allow programs to talk to Microsoft Mail applications like Exchange Server. |
| MB |
Megabyte: Mega means 10 to the power 6, or 1,000,000 bytes, however in computing terms we work in binary so it worked out as 2 to the power 20, which equals 1,048,576 bytes. |
| MD5 |
Message digest algorithm 5: Produces a fixed 128 bit hash commonly used to check integrity of files |
| MKV |
Matroska Files: these are video files, similar to AVI files, but with extra features. |
| MMC |
Microsoft Management Console: A front end that accepts various “Snap ins” for managing items in a windows environment. |
| MP3 |
MPEG-1 Audio Level 3: A popular format for storing and playing digital music. |
| MPEG |
Moving Picture Expert Group |
| MPF |
Modular Policy Framework: A system for applying policies on a Cisco Firewall they can be applied globally or per interface. |
| MSA |
Modular Storage Array: A range of SAN devices by Hewlett Packard |
| MSCHAP |
The Microsoft Implementation of CHAP |
| MSDE |
Microsoft SQL Desktop Edition: A cut down version of Microsoft SQL Server,that is free. Has now been replaced by SQL Express. |
| MSDN |
Microsoft Developer Network (here). |
| MSI |
Microsoft Installer File: A type of file extension that denotes a piece of setup software for an application, the advantage of .msi files is that they can be installed on clients via GPO |
| MTU |
Maximum Transmission Unit: The maximum size (in bytes) that a single packet can be, for transmission over a network. |
| MX |
Mail exchanger record: Is a DNS record that it used so that someone can query a domain to find the name/address of its mail server. |
| NAP |
Network Access Protection: A Microsoft technology for controlling network access based on policies. |
| NAS |
Network Attached Storage: Hard drive storage that’s presented to a network with its own address. |
| NAT |
Network Address Translation: Translating many IP addresses to few IP addresses. |
| NDR |
Non Delivery Report: Produced by a mail server, and sent to the sender, when an email cannot be delivered. |
| NetBIOS |
Network Basic Input/Output System: Is NOT a networking protocol its an API, can be likened to DNS insofar at it maps names to IP addresses. |
| NFS |
Network File system: Developed by Sun Microsytems this is a protocol for allowing a client to access files on a shared datastore/system, currently at version 4 and is defined in RFC 3530. |
| NIC |
Network Interface Card: The device that connects a PC/Server to a network this can be wired or wireless. |
| NNTP |
Network News Transfer Protocol: An old protocol used for posting usenet articles runs on TCP port 119 |
| NSEL |
NetFlow Secure Event Logging |
| NTFS |
New Technology File system: Introduced with Windows NT4, a method of securing files on storage media. |
| NT |
New Technology: Released as Windows NT 3.1 (1993). The most well known is Windows NT4 (1996). Its still a system in use today (Windows 7 and Server 2008 R2 is denoted as NT 6.1). |
| NTLM |
NT LAN Manager: A Microsoft suite of protocols that provide authentication, integrity and confidentiality. |
| NTP |
Network Time Protocol: Used to synchronise system clocks on network devices. It runs over UDP port 123. |
| NVRAM |
Non-Volatile RAM: A term usually used with routers to describe RAM that contains information that will not be lost when the device is powered off, these days we would call it flash memory. But you will still see this term used in router documentation. |
| OAB |
Offline Address Book: Generated by Microsoft Exchange Server and downloaded to Microsoft Outlook clients for use in cached mode. |
| OCSP |
Online Certificate Status Protocol: Used by a CA to publish a CRL. |
| ODBC |
Open Database Connectivity: A standard method of accessing a database. Usually configured on a client that has software that needs a database ‘back-end’ on another server or machine, |
| OEM |
Original Equipment Manufacturer: Someone who produces computer equipment that comes pre-bundled with a Windows operating system. Note: A Windows OEM code will NOT work on Volume Licensed Software |
| OOBE |
Out Of Box Experience: The name Microsoft gives to the process you go through when you first setup a copy of Windows. |
| OS |
Operating System: The software between the hardware and you, on a PC it would be Windows or Linux, on a Hardware device it is probably vendor specific i.e. Cisco ASA OS 7.2(2) |
| OTP |
One Time Password: Used in cryptography to obtain a certificate. |
| OU |
Organisational Unit: This is a container used in Directories like Active Directory or Novell Directory Services, can be used to hold directory objects like users, servers or printers etc. They can also be used to apply GPO |
| OVF |
Open Virtualisation Format: A method of “Transporting” virtual machines, used so that they can be made “Portable”. |
| OWA |
Outlook Web Access: The web front end to Microsoft Exchange. After Exchange 2010 this is now called Outlook Web App. |
| P2V |
Physical to Virtual: The act of converting a real machine top a virtual one. |
| PAK |
Product Activation Key: a License key used by Cisco, to enable/add features to a Cisco device. |
| PAP |
Password Authentication Protocol: Used to authenticate users before network access is allowed. |
| PAT |
Port Address Translation: Translating many IP addresses to a single IP address (Used on Cisco firewalls for port forwarding). |
| PCL |
Printer Control Language: Is a command language that is used with printer drivers so that applications can send data to a printer. |
| PCoIP |
Created by a firm called Teradici, it is a similar protocol to RDP, insofar as it lets you view the desktop of a remote machine and interact with it. It’s the preferred protocol to use with VMware View (after version 4.6). |
| PDC |
Primary Domain Controller: Used in Windows NT4 environments, though now in new Active Directory you will still have a domain controller that holds the PDC Emulator FSMO role. |
| PDF |
Portable Document Format: Usually opened with Adobe Acrobat (Though other pdf readers exist). |
| PDM |
PIX Device Manager: Web management console for Cisco firewalls running OS 6 and below. |
| PEM |
Privacy Enhanced Mail: A format for showing a digital certificate, can be sent via email or pasted into a devices configuration looks like this. |
|
PERC |
PowerEdge Expandable RAID card: Dell’s name for its server RAID cards. |
| PFS |
Perfect Forward Secrecy is a method by which new keys are generated, each new key is mathematically linked to the key that came before it, the prior key being a “Grandfather” key. With PFS enabled this link is broken so a key can not be forward/reverse engineered to guess a previous/new key value). Every new negotiation produces a new fresh key. |
| PHP |
PHP:Hypertext Processor (confusing eh? The first word of the acronym is the acronym, this is called a recursive acronym). Its an embedded scripting language commonly used in HTML. |
| PID |
Process Identifier: The number allocated to processes on a computer running an OS like windows or UNIX. |
| PING |
Ping is a command utility that uses the “echo request” part of the ICMP suite of communications protocols, it is used to test network connectivity and the “round trip” time packets take over a network. |
| PIX |
Packet Internet eXchange: Cisco’s firewall platform before the ASA was released. |
| PKI |
Public Key Infrastructure: A system that uses public and private keys for cryptography. Commonly used for digital certificates. |
| POE |
Power Over Ethernet: A method of delivering electric power over a network cable. Used to power devices like IP Phones and Wireless Access Points |
| POP |
Post Office Protocol: Method for retrieving mail from a public mail server runs over TCP port 110 |
| POTS |
Plain Old Telephone System. |
| PPP |
Point to Point Protocol: This is a communication protocol that is designed to establish a link between two places, it provides authentication, encryption and compression. |
| PPPoA |
Point to Point Protocol over ATM: This is a communication protocol that uses PPP and places , it’s commonly used with ADSL routers. |
| PPPoE |
Point to Point Protocol over Ethernet: This is a communication protocol that uses PPP and places that information into normal ethernet frames, it’s commonly used with DSL and FTTC connections. |
| PPTP |
Point to Point Tunnelling Protocol: Used to establish a VPN tunnel it runs in IP protocol 47 and TCP port 1723. |
| PSOD |
Pink Screen Of Death: Seen on VMware servers after a crash (like a Windows BSOD only the screen background is pink). |
| PST |
A Microsoft Personal Folder File: Usually used by Microsoft Outlook to store mail locally in a file. These can go corrupt/get deleted and cause loss of data, which unlike the data in your email server may not be backed up! |
| PSTN |
Public Switched Telephone Network: Old fashioned phone system sometimes referred to as POTS |
| PXE |
Pre eXecute Environment: A system in modern PC’s that enable them to be booted from their NIC. |
| R2 |
Release 2 (or Second Release), used by Microsoft for major OS releases e.g. Windows Server 2003 R2 and Windows Server 2008 R2 |
| RAID |
Redundant Array of Independent Disks (or Inexpensive Disks depending on who you are talking to). This is a blanket term, for any method of presenting multiple physical disks, and making them appear as a single piece of storage. |
| RADIUS |
Remote access Dial In User System: A method of authenticating access to a network. |
| RAM |
Random Access Memory: Or volatile memory, provides a PC/server with short term high speed memory. |
| RARP |
See ARP |
| RBAC |
Role Based Access Control: Used with Exchange 2010, makes delegating Exchange tasks easier. |
| RBL |
Relay Block List / Reatlime Blackhole List: A dynamic list of IP addresses and host-names that have been suspected/reported as being either an open relay, or are generating spam. |
| RBSU |
ROM Based Setup Utility: Typically found on HP Servers the RBSU is a small BIOS chip for holding the system settings. |
| RC4 |
Is a cypher developed by RSA it is easily broken by modern computers thus considered insecure. |
| RD |
Remote Desktop, See RDP |
| RDP |
Remote Desktop Protocol: A Microsoft protocol that allows the desktop of one machine, to be shown on another machine over a network, can be used for remote assistance, remote administration, or Terminal Services. Runs over TCP port 3389 |
| RDS |
Remote Desktop Services the new name in Windows 2008 for Terminal Services (TS). |
| RDX |
Removable Disk Storage/Backup System (No I don’t know why it has an X!) a Hard Drive based backup solution that behaves like a tape drive. |
| RFC |
Request For Comments: These are a collection of memorandums published by the IETF as a method of trying to standardise communication standards and protocols. |
| RIS |
Remote Installation Services: Introduced in Windows 2000, system for deploying (imaging) PC’s and Servers from a central Windows Server (Replaced by WDS). |
| RJ45 |
Registered Jack 45: Is a standard 8 pin network connection. |
| RODC |
Read Only Domain Controller (Server 2008 only). A domain controller with a “Read Only” database it caches credentials rather than storing then in case it is stolen. |
| ROM |
Read Only Memory: Memory that can not (normally) be written to i.e. CD ROM. |
| ROMMON |
ROM Monitor, is a low level bootstrap program used on Cisco devices to check and initialise the hardware then load the operating system. |
| RPC |
Remote Procedure Call: A system used on random communication ports to let systems talk to each other. |
| RRAS |
Routing and Remote Access: Is a Windows server role, that provides the following, Remote access, Dial up, VPN, NAT, Routing, and Demand Dial services. |
| RSA |
Rivest, Shamir and Adleman: An algorithm for public key cryptography. |
| RSAT |
Remote Server Administration Tools: Suite of Microsoft MMC consoles for managing servers and domains. |
| RSS |
Really Simple Syndication: A web based news feed system. |
| RTFM |
Read the F***ing Manual! |
| RTFQ |
Read the F***ing Question! |
| RTM |
Released To Manufacturing |
| SA |
Security Association: a secured peer in a site to site VPN |
| SAN |
Storage area Network: A Network of storage/disks that is presented as central storage to many devices.
Subject Alternative Name: These are additional names added to a digital certificate, they are used on web server certificates, and unified communications certificates. |
| SAS |
Serial attached SCSI used for connecting computer peripherals, currently runs at about 3 Gbps but can run up to 10 Gbps. |
| SATA |
Serial ATA: A Standard for connection drives, (Hard Drives and optical drives) its a seven pin socket that connects them to the computers motherboard. |
| SBS |
Small Business Server: A Microsoft Server platform that includes Exchange (and with some flavours ISA and SQL Server) as the name suggests, for small corporate deployments with less than 75 users/devices |
| SCCM |
System Center Configuration Manager: Formally (SMS) Systems Management Server this is a tool for managing large numbers of Windows Machines. |
| SCCP |
Skinny Client Control Protocol: A Cisco proprietary telephony protocol. |
| SCP |
Secure Copy: Is a system the relies on SSH and runs over TCP Port 22 to move files from/to a machine securely |
| SCSI |
Small Computer System Interface: A set of commands for transferring data between hardware devices, traditionally 8 or 16 devices can be attached to a SCSI bus. |
| SD |
Secure Digital: A memory card format developed by Panasonic .Basically a small flash memory card also comes as miniSD and microSD. In addition you can also get SDHC and SDXC. |
| SDHC |
SD High Capacity – up to 32 GB capacity. |
| SDM |
Security Device Manager: A web based management tool for Cisco Routers. |
| SDXC |
SD Extended Capacity – up to 2 TB capacity. |
| SHA |
Secure Hashing algorithm: Produces a fixed 160 bit hash commonly used to check integrity of files |
| SID |
Security Identifier: A string of letters and numbers assigned to a windows client as it joins a domain. with older machines there was much panic about needing to strip the SID fro cloned or imaged machines. These days its less of a problem (click here.) |
| SIM |
System Image Manager: Is both part of the ADK and the WAIK and used to produce unattended XML answer files for Windows deployment |
| SIP |
Session Initiation Protocol: Used for video, voice, and chat networking. |
| SMB |
1. Small to Medium sized Business: Also a Cisco Partner Level.
2. Server Message Block: An old Microsoft file sharing protocol, now renamed CIFS |
| SMS |
Systems Management Server: this is a tool for managing large numbers of Windows Machines, it’s now been replaced with SCCM. |
| SMTP |
Simple Mail Transfer Protocol: Common protocol used for email runs on TCP port 25 |
| SNMP |
Simple Network Management Protocol A widely used network monitoring and control protocol. Uses UDP ports 162 and 161. |
| SOHO |
Small Office / Home Office |
| SPAP |
Shiva Password Authentication Protocol: A simple password encryption protocol, used with Windows Server 2003 onwards. |
| SPF |
Sender Policy Framework: |
| SPx |
Service Pack x: Usually written as SP1 for Service Pack 1, SP2 for Service Pack 2 etc. |
| SPI |
Security Parameter Index: Label used by IPsec for the end of a VPN tunnel in phase 2 of IKE 2 unidirectional tunnels are created each will have its own SPI number. |
| SQL |
Structured Query Language: Typically a Database system/server, most well known is Microsoft SQL server, or the free MySQL alternative. |
| SRV |
Service Locator: A type of DNS record that lets clients on a network, know where services are, and how to access them. |
| SSH |
Secure Sockets Handshake: A secure method of console access, think of it as secure telnet. |
| SSID |
Service Set Identifier: Then name of a Wi-Fi network. can be set to either broadcast (visible), or be hidden. But it is still visible in the wireless packets that can be ‘sniffed’ so even a half determined attacker will be able to get it. |
| SSL |
Secure Socket Layer: A cryptographic system that used public and private keys to transmit data over a network securely. |
| SSTP |
Secure Socket Tunneling Protocol: This essentially allows the use of L2TP and PPP protocols, but does it over TCP port 443 (usually for https). This means it is usually an open port at remote/home locations. |
| SLA |
Service Level Agreement: An agreement between an IT support organisation and a user of its/their services. OR a command used in Cisco IOS to set up a monitor. |
| STP |
Spanning Tree Protocol: A system used on network switches to avoid “loops” |
| TAC |
Technical Assistance Center: Cisco’s third line support, be sure to have a valid support agreement before you ring. |
| TAR |
Tape Archive: A file extension for compressed files common formats are .tgz .gzip, or .bzip2 |
| TB |
Terabyte: Tera means 10 to the power 12, or 1,000,000,000,000 bytes, however in computing terms we work in binary so it worked out as 2 to the power 40, which equals 1,099,511,627,776 bytes. |
| TCP |
Transmission Control Protocol: Connection oriented protocol for data transfer, uses a “3 way handshake” to make sure the traffic gets where its supposed to go. |
| TELNET |
Terminal NETwork: A TCP protocol that allows remote users to enter commands on a device runs over TCP port 23. |
| TFTP |
Trivial File Transfer Protocol: A Little like FTP, but uses UDP Port 69, commonly used for updating firmware on network devices. |
| TKIP |
Temporal Key Integrity Protocol: Used on Wi-Fi networks, usually with WPA to improve the security of the earlier WEP protocol. |
| TLS |
Transport Layer Security:Similar to SSL provides encrypted data transfer |
| TS |
Terminal Services: Microsoft’s “Thin Client” solution for sharing applications. Now called Remote Desktop Services on Server 2008. |
| UAC |
User Account Control: Introduced with Windows Vista, a system designed to stop you running normally with an administrative account |
| UCS |
Universal Character Set: A method of encoding characters so thay can be sent digitally. |
| UDP |
User Datagram Protocol: This is a a transport protocol which operates at the same layer as TCP but unlike TCP it is not connection based, it’s a “Fire and forget” protocol if it does not get to the other end its not important. |
| UNC |
Universal Naming Convention: Used to map network drives and resources e.g. \\server_name\share_name\file_name |
| UPS |
Uninterruptible Power Supply: A device that provides battery backup power when the electrical power fails or drops to an unacceptable level. |
| URL |
Uniform Resource Locator: a Web address like www.petenetlive.com |
| USB |
Universal Serial Bus: A Method of connecting computer peripherals (up to a maximum of 127 devices). USB 1.0 is 1.5Mbps, USB 1.1 is 12Mbps, USB 2 is 480 Mbps and USB 3.0 is 4800 Mbps. |
| UTC |
Universal Time Coordinated (Commonly Coordinated Universal Time) is the time taken from Greenwich this can also be called “Zulu Time”. |
| UTF-8 |
UCS Trasformational Format (8bit) A system for encoding characters so they can be sent digitally |
| VAMT |
Volume Activation Management Tool: A Microsoft tool for managing MAK software licence keys. This can also change KMS keys to MAK keys. |
| VB |
Visual Basic: A Microsoft programming language. Also used with VBScripting, which uses files with a .vbs extension to run scripts |
| VC |
Virtual Center: A Server that manages your VMware ESX hosts |
| VI3 |
Vmware virtual infrastructure version 3 |
| VI |
Virtual Infrastructure. |
| VIB |
VMware installation bundle: software and driver packages needed for installing ESX5 |
| VIM |
Virtual Infrastructure Manager: or VMware vCenter |
| VLAN |
Virtual LAN: A group of network devices that appear to be on a separate network segment, also called a broadcast domain. |
| VLK |
Volume Licence Key: Windows XP/Windows Server 2003 (And earlier) used these keys for multiple activations, they have been replaced with MAK and KMS Keys |
| VLSC |
The Microsoft Volume Licence Service Center, formally called eOpen (here) |
| VM |
Virtual Machine: A group of files that when read by some software like VMware, VirtualPC, Hyper-V, or XenServer looks and behaves like a real physical machine. |
| VMDK |
Virtual Machine Disk: VMware format for storing hard drives for virtual machines. |
| VMFS |
Vmware file system: Used so that multiple hosts can access the same storage at the same time, it uses a system of “Locks” on each file so only one host access the data at any one time. |
| Vmotion |
A Vmware system for moving a running virtual machine from one ESX host to another ESX host. You can also use “Storage Vmotion” to move a running virtual machine’s files and hard disks to another piece of storage. |
| VPN |
Virtual Private Network: A secure link that carries sensitive data over a public network, the data is protected by encryption. |
| VPS |
Virtual Private Server: A VM that provided for you for a monthly or yearly fee. |
| vSphere |
VMware’s cloud operating system formally called VI3 |
| VSC |
Virtual Service Community: Used on HP wireless networks this is a collection of network settings. |
| VSS |
Windows Volume Shadow Services: System used by Microsoft for backing up data. |
| VT-x |
Intels processor Visualization technology, Originally code named “Vanderpool” it needs to be enabled on some machines in their BIOS/RBSU/CMOS |
| WAIK |
Windows Automated Installation Kit: A suite of tools from Microsoft for imaging and deploying Windows systems. With Windows 8 this has now been replaced with the ADK |
| WAN |
Wide Area Network: A network that connects geographically distributed LANs. Also the external port on a router or firewall. |
| WAP |
Wireless Access Point,: A Device for connecting wireless network hosts to a wired network, or for ‘bridging’ them onto another network. |
| WCF |
Windows Communication Framework: This is a Windows Server 2008 feature that runs under .net |
| WDS |
Windows Deployment Services: A system for deploying (imaging) PC’s and Servers from a central Windows Server (Replacement for RIS). |
| WEP |
Wired Equivalent Privacy: A security protocol used by Wi-Fi networks. Its not considered as secure as WPA, because of an inherent fault in the way it uses RC4 to generate keys. Its easily defeated and should NOT be used to protect sensitive data. |
| Wi-Fi |
Wireless Fidelity: A term used to describe various net worked devices on a WLAN connected wirelessly. |
| WindowsPE |
Windows Pre-Execution Environment: A cut down version of Windows that can be run from USB drive, CD, or deployed from WDS. |
| WINS |
Windows Internet Naming Service: A legacy Microsoft method of resolving computer NETBIOS names on a network. |
| WLAN |
Wireless Local Area Network (See LAN) |
| WMI |
Windows Management Instrumentation: Is a system that programmers can use to talk to and get information from Windows systems. And also to remotely manage those systems. |
| WPA |
Wi-Fi Protected Access: A security protocol used to secure wireless networks, its considered more secure than its predecessor WEP, because WPA uses TKIP integrity to change the secure key used. It can also use EAP. |
| WSUS |
Windows Server Update Services: Free update and patch management system for Windows servers and applications. |
| WWW |
World Wide Web: A collection of text and graphics displayed in a web browser, what most people would call the internet.
www is also the Cisco reference to TCP Port 80 (http) |
| XBMC |
XBOX Media Center: Software originally developed for the XBox, but now available for install to Windows and Linux as a Media Center Suite. |
| XML |
eXtensible Markup Language:A structured way of presenting information, that uses tags much like HTML |
| ZAK |
Zero Administration Kit: Introduced with Windows NT4. |
| ZIP |
A term used to describe the process of compressing many files/folders and putting then in a compressed “Archive” folder. “.zip” is a file extension for an archive though there are more archive types, e.g. .RAR, .CAB, and .TAR are common examples. |
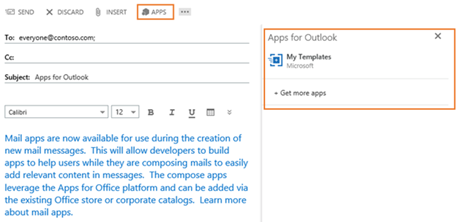
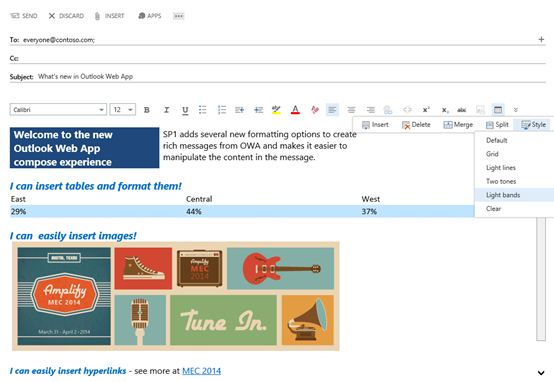 Apps for Office in Compose – Mail apps are now available for use during the creation of new mail messages. This allows developers to build and users to leverage apps that can help them while they are composing mails. The compose apps leverage the Apps for Office platform and can be added via the existing Office store or corporate catalogs. Learn more about Apps for Office.
Apps for Office in Compose – Mail apps are now available for use during the creation of new mail messages. This allows developers to build and users to leverage apps that can help them while they are composing mails. The compose apps leverage the Apps for Office platform and can be added via the existing Office store or corporate catalogs. Learn more about Apps for Office.
 Note:
Note: